Automation to Enhance Cybersecurity
Introduction
As digital crimes grow both more sophisticated and frequent, the security operations must evolve to be ever-more proactive, responsive, and automated. Here is where strong open-source tools like Wazuh and n8n come in. Wazuh offers enterprise-grade monitoring, and n8n dispenses with the burden of workflow automation. Together, they provide a strong framework for real-time threat detection and automatic incident response.
What is Wazuh?
Wazuh is a security platform (SIEM/XDR) that can be used for:
• Log analysis and threat detection
• Intrusion detection (HIDS)
• File integrity monitoring
• Vulnerability detection
• Security configuration assessment
• Alerting in real-time depending on the rules configured
It is largely used for monitoring servers, endpoints, containers, and cloud environments.
What is n8n?
n8n is an open-source workflow automation tool designed for connecting a wide range of services and APIs without having to write loads of code. It supports:
• More than 350 integrations, including HTTP, databases, messaging platforms, and cloud services
• Workflows to be triggered by webhooks or schedules
• Custom logic using JavaScript or conditional nodes
• Full REST API support
• Self-hosting for privacy and control
Benefits of Integration
✅ Instant automated response to threats
✅ Reduced response time and human intervention
✅ Enhances visibility into ongoing threats
✅ Multiple channels for alerting and escalation
✅ Works with your existing tools and infrastructure
✅ Scalable and flexible, and fully open-source
How Integration Works
1. Configure Wazuh to Send Alerts
You may configure Wazuh to send alerts to an external script or webhook. This can be configured in the ossec.conf file, or it may be configured through a custom alert processor script.
2. Setup Webhook in n8n
• Create a new workflow in n8n with a Webhook node
• Allow it to receive POSTs from Wazuh alerts
• Parse the JSON data and feed it through the logic nodes (IF, Switch, Set)
3. Responding Actions
You could:
• Send messages (Telegram, Slack, Email)
• Block the IP address
• Restart compromised services
• Open a support ticket
• Integrate with security dashboards
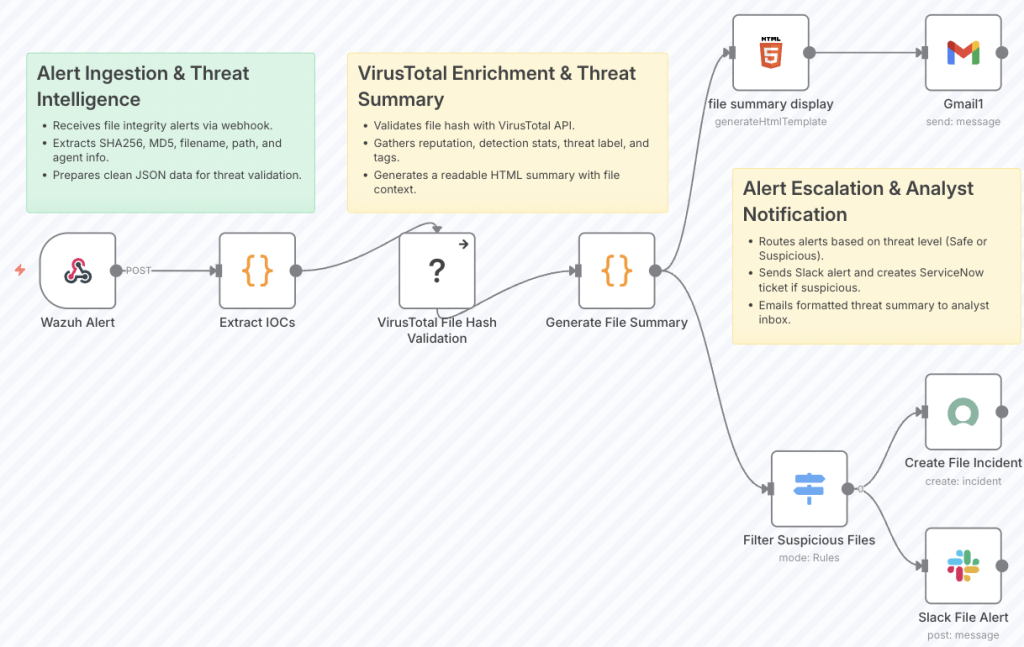
Practical Example: Malicious File Detection and Automated Response
A real-world example of this integration can be seen in this published n8n workflow. It demonstrates how a Wazuh alert triggered by a malicious file detection is automatically forwarded to n8n.
The workflow performs the following:
• Receives the alert via webhook
• Submits the file hash to VirusTotal for threat intelligence analysis
• Parses the VirusTotal results
• Sends a real-time alert with the results to a Slack channel
This workflow not only automates threat validation but also ensures immediate team awareness—demonstrating a practical, low-effort method of enhancing your SOC capabilities using open-source tools.
Conclusion
The use of Wazuh for detection and n8n for automation represents a modern way of achieving efficiency and proactivity in cybersecurity. This integration increases your organization’s defense posture while freeing your team to work on incidents that truly matter.
The potential foundation for automated security operations that this duo provides is valuable for both the DevOps team and an enterprise security group.
